
Do you ever wonder how cybersecurity experts protect computer systems from potential threats? Are you intrigued by the world of hacking and want to explore it ethically? If so, you’re in the right place. In this article, we will guide you through the process of learning ethical hacking from scratch in 2024.
With cybercrime on the rise and organizations seeking skilled professionals to safeguard their sensitive data, the demand for ethical hackers has never been higher. But how can you, with no prior experience, learn ethical hacking and make a significant impact in the field of cybersecurity?
Prepare to embark on an exciting journey, as we provide you with a step-by-step guide on how to get started with ethical hacking. From understanding the basics to discovering online resources and beginner-friendly courses, we have everything you need to kickstart your journey as an ethical hacker.
Also read: Get The Complete 2024 Web Development Bootcamp (moumentec.com)
Key Takeaways:
- Learn the basics of ethical-hacking and its importance in the digital landscape.
- Discover a variety of online resources and communities dedicated to ethical-hacking.
- Explore beginner-friendly courses that will help you develop your skills in ethical hacking.
- Apply your knowledge in practical scenarios to strengthen your skills and understanding.
- Approach ethical-hacking responsibly and advocate for cybersecurity awareness.
Understanding Ethical Hacking
Before diving into the world of ethical-hacking, it’s important to understand the basics. In this section, we will explore what ethical-hacking is, its importance in today’s digital landscape, and how it differs from malicious hacking. You will also learn about the ethical hacker’s role in safeguarding computer systems and networks from potential threats.
The Basics of Ethical Hacking
Ethical-hacking, also known as penetration testing or white hat hacking, involves identifying vulnerabilities in computer systems and networks for the purpose of improving security. Ethical hackers, legitimate professionals with extensive cybersecurity knowledge, use their skills to identify and fix potential weaknesses before malicious hackers can exploit them.
Importance in Today’s Digital Landscape
In today’s interconnected world, where digital attacks and data breaches are on the rise, ethical hacking plays a critical role in safeguarding our online assets. Organizations, including governments and corporations, rely on ethical hackers to proactively assess and strengthen their security systems, mitigating the risk of cyber attacks.
Ethical Hacking vs. Malicious Hacking
While both ethical hacking and malicious hacking involve exploiting vulnerabilities, the intent behind each is vastly different. Ethical hackers operate with the consent of the system owner, using their skills to improve security measures and protect against potential threats. On the other hand, malicious hackers, also known as black hat hackers, engage in illegal activities such as stealing information, spreading malware, or causing disruption.
The Ethical Hacker’s Role
An ethical hacker often works closely with organizations to conduct vulnerability assessments, penetration testing, and security audits. Their goal is to identify and address weaknesses in computer systems and networks, ensuring that robust security measures are in place to safeguard sensitive data and protect against potential cyber attacks.
Online Resources for Ethical Hacking

Looking to enhance your skills in ethical hacking? In this section, we will introduce you to some of the best online resources available. Whether you’re a beginner or looking to advance your knowledge, these resources will provide you with the necessary tools and support for your ethical-hacking journey.
Also read: 100 Days of Code: Learn Easily Web Development Bootcamp (moumentec.com)
1. Tutorials and Forums
One of the best ways to learn ethical hacking is by accessing tutorials and participating in forums. Websites like Cybrary and Hack Forums offer a wide range of tutorials, guides, and discussions on ethical hacking techniques, tools, and case studies. These platforms provide valuable insights from experienced professionals, allowing you to get hands-on experience and learn from real-world examples.
2. Online Classes and Certifications
If you prefer a more structured approach to learning, online classes and certifications are an excellent option. Platforms like Udemy and Coursera offer comprehensive courses taught by industry experts. These courses cover various aspects of ethical hacking, from the fundamentals to advanced techniques. By completing these courses, you can enhance your skills and earn certifications that validate your knowledge and expertise.
3. Websites and Platforms
There are several websites and platforms dedicated to providing ethical hacking resources and information. OWASP (Open Web Application Security Project), for example, offers a wealth of knowledge on web application security and ethical-hacking methodologies. HackThisSite is another platform that provides challenges and tutorials for aspiring ethical hackers to sharpen their skills.
Additionally, online communities like Reddit’s r/AskNetsec and Stack Exchange’s Information Security, are great places to ask questions, share experiences, and connect with fellow ethical hackers. These communities create a supportive network where you can exchange ideas, seek advice, and stay updated with the latest trends in ethical hacking.
To sum it up, the abundance of online resources for ethical-hacking ensures that you can find the learning materials and support you need. Remember to explore tutorials and forums, enroll in online classes, and utilize dedicated websites and platforms. This comprehensive approach will help you build a strong foundation and excel in the field of ethical hacking.
Beginner-Friendly Ethical Hacking Courses

If you prefer a structured approach to learning ethical hacking, enrolling in a beginner-friendly course is an excellent option. These courses are designed specifically for beginners, providing a comprehensive introduction to the fundamentals of ethical hacking. By enrolling in one of these courses, you can gain the knowledge and skills necessary to start your journey in cybersecurity.
Top Ethical Hacking Courses for Beginners
Below, we have highlighted some of the top ethical-hacking courses that are perfect for beginners:
- Course 1: “Introduction to Ethical Hacking”
- Course 2: “Ethical Hacking Essentials”
- Course 3: “Web Application Penetration Testing”
- Course 4: “Learn Ethical Hacking from Scratch 2024”
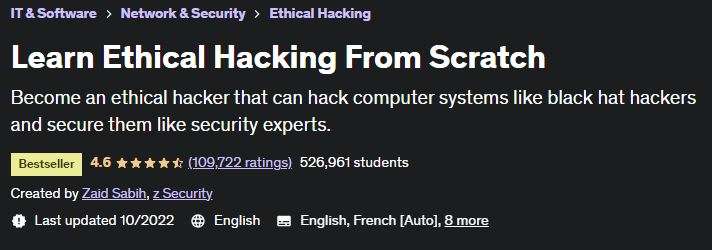
About this course Learn Ethical Hacking from Scratch 2024
- language: english
- Teacher: Zaid Sabih
- Number of lessons: 146 lessons
- Duration: 15 hours and 54 minutes
- Can be played on: Windows, Mobile, TV
**Course download link Learn Ethical Hacking from Scratch 2024**
One Drive
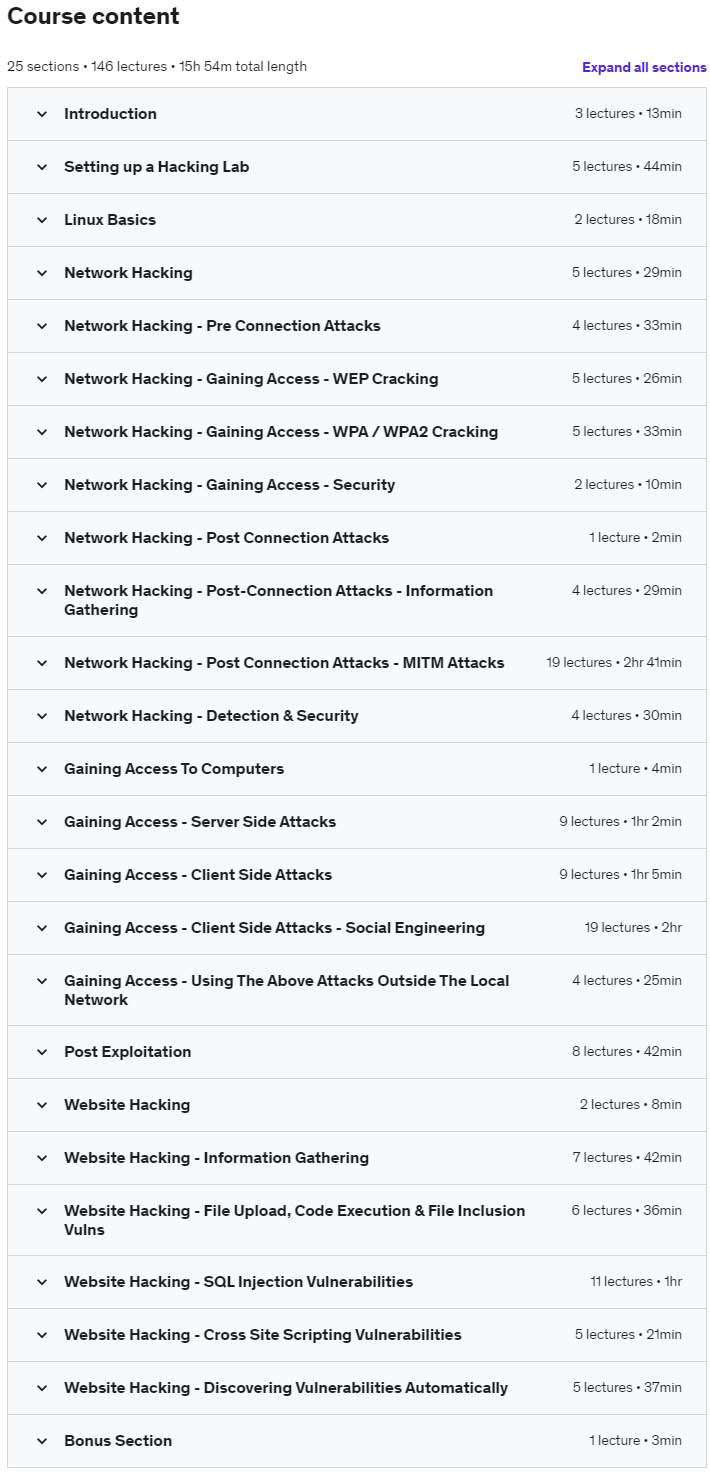
Each of these courses provides a structured learning experience with well-defined learning objectives. You can expect to gain practical skills, theoretical knowledge, and hands-on experience in a supportive learning environment. Choose the course that aligns with your goals and learning style to embark on your ethical hacking journey.
Practical Learning and Application
Now that you have a solid foundation in ethical-hacking, it’s time to apply your knowledge in practical scenarios. In this section, we will guide you through hands-on exercises and provide practical examples to strengthen your skills in ethical hacking.
You will learn about common hacking techniques, tools utilized by ethical hackers, and how to conduct vulnerability assessments to identify and fix security flaws. By understanding these techniques and tools, you will be better equipped to safeguard computer systems and networks from potential threats.
Hands-On Exercises
One of the best ways to learn ethical hacking is through hands-on exercises. By practicing in a controlled environment, you can apply your knowledge and gain valuable experience.
Start by setting up a virtual lab where you can safely perform different hacking techniques. You can use platforms like VirtualBox or VMware to create virtual machines and simulate real-world scenarios.
- Practice footprinting and reconnaissance techniques to gather information about a target system.
- Learn how to scan networks and identify potential vulnerabilities.
- Explore different types of attacks, including social engineering, phishing, and password cracking.
- Discover the ins and outs of network sniffing and packet analysis.
Remember, ethical hacking should only be performed on systems and networks you have legal authorization to test. Always follow proper ethical guidelines and respect the privacy and security of others.
Tools Utilized by Ethical Hackers
As an ethical hacker, you will need to familiarize yourself with various tools and software commonly used in the field. These tools can assist you in identifying vulnerabilities and securing systems. Here are some essential tools you should explore:
- Nmap: A powerful network scanning tool used for network exploration and security auditing.
- Metasploit Framework: A widely-used penetration testing platform for discovering vulnerabilities and exploiting them.
- Wireshark: A network protocol analyzer for capturing and analyzing network traffic.
- OWASP ZAP: An open-source web application security scanner used to identify vulnerabilities in web applications.
These tools, along with many others, will help you gain a deeper understanding of the technical aspects of ethical hacking and enable you to conduct comprehensive security assessments.
Conducting Vulnerability Assessments
One of the key tasks of an ethical hacker is to conduct vulnerability assessments to identify and fix security flaws. This involves a systematic evaluation of software, systems, and networks to determine potential weaknesses. Here is a step-by-step process you can follow:
- Planning: Define the scope of your assessment and gather relevant information about the target system.
- Scanning: Perform a thorough scan of the network and system using tools like Nmap to identify open ports and services.
- Enumeration: Gather as much information as possible about the target system, including user accounts, file shares, and network configurations.
- Vulnerability Assessment: Utilize tools like Nessus or OpenVAS to identify vulnerabilities and potential security weaknesses.
- Exploitation: Safely exploit identified vulnerabilities to demonstrate their impact and provide recommendations for mitigation.
- Reporting: Prepare a detailed report highlighting the vulnerabilities discovered, their risk level, and recommendations for remediation.
By following these steps, you can effectively assess the security of a system and provide actionable recommendations to enhance its security posture.
Conclusion
In conclusion, learning ethical hacking from scratch in 2024 can be an exciting and rewarding journey. By understanding the basics of ethical hacking, exploring online resources, enrolling in beginner-friendly courses, and applying your knowledge in practical scenarios, you can become a proficient ethical hacker.
Remember to always approach ethical hacking with a responsible mindset, advocating for cybersecurity awareness and protection. As you embark on your journey, stay updated with the latest industry trends and continue expanding your knowledge and skills in ethical hacking to stay ahead of potential threats.
Start your journey today and become a valuable asset in the world of cybersecurity. With dedication and continuous learning, you can make a real difference in safeguarding computer systems and networks and contribute to a safer digital environment for all.
FAQ
Can anyone learn ethical hacking from scratch?
Yes, anyone with an interest in cybersecurity and the willingness to learn can start their journey in ethical hacking. It is important to have a strong foundation in computer systems and networking, but anyone can acquire the necessary skills through dedicated learning and practice.
What is the difference between ethical hacking and malicious hacking?
Ethical hacking, also known as penetration testing or white hat hacking, is performed legally and ethically to identify vulnerabilities in computer systems and networks. Malicious hacking, on the other hand, is conducted with harmful intent to exploit these vulnerabilities for personal gain or to cause harm. Ethical hacking aims to safeguard systems and protect them from potential threats.
Are there any online resources available for learning ethical hacking?
Yes, there are numerous online resources available for learning ethical hacking. These include tutorials, forums, online classes, and certifications. Reputable websites and platforms dedicated to ethical hacking provide valuable resources and communities where beginners can learn, interact, and enhance their skills.
What are some beginner-friendly courses for learning ethical hacking?
There are several beginner-friendly courses tailored for individuals who are new to ethical hacking. These courses cover the fundamentals of ethical hacking, teach various hacking techniques, and provide hands-on practical exercises. Some popular beginner courses include Certified Ethical Hacker (CEH), CompTIA Security+, and EC-Council Certified Ethical Hacker (CEH) Certification.
How can I apply my knowledge of ethical hacking in practical scenarios?
Applying your knowledge of ethical hacking in practical scenarios is essential for gaining practical experience. You can start by conducting vulnerability assessments on computer systems and networks, identifying security flaws, and proposing solutions to fix them. Practicing with simulated environments and participating in ethical hacking challenges can also enhance your skills.
What is the responsible approach to ethical hacking?
When engaging in ethical hacking, it is crucial to approach it with a responsible mindset. This involves obtaining proper authorization before performing any security assessments, respecting privacy and confidentiality, adhering to ethical guidelines, and reporting any discovered vulnerabilities to the rightful owners for remediation. Responsible ethical hackers prioritize cybersecurity awareness and protection.


![15+ Best Oxford University Executive Education Programs [2025 September] » Courses and Programs 15+ Best Oxford University Executive Education Programs [2025 September]](https://moumentec.com/wp-content/uploads/2025/09/15-Best-Oxford-University-Executive-Education-Programs-2025-September-220x150.png)
![12 Best + Free Stanford Courses & Certificate [2025 September] » Courses and Programs 12 Best + Free Stanford Courses & Certificate [2025 September]](https://moumentec.com/wp-content/uploads/2025/09/12-Best-Free-Stanford-Courses-Certificate-2025-September-220x150.jpg)

